IAM Root Users Monitoring
Each AWS account is registered with an unique email address. The accounts can be created via AWS Organizations or individually outside of AWS Organizations. Each AWS account has a root user, named <root_user>. The root user is a very powerful user with complete access to the account.
IAM Root Users best practices
- Use a group email instead of personal email for AWS Account registration
- Protect the email domain and email account
- Disable the root user
- Create a separate admin user instead for day-to-day activities.
- Protect root user with MFA
- Do not use AWS access keys
- Keep track of console access for root users
CloudYali brings information for all root users across your cloud in one place. Now you can see all the details about your root users such as:
- MFA active status
- Access Keys (Key1 and Key2) Status
- Inline and Attached Policies
- Signing Certificate
- Password status
Supported root user information
All root users details
Having comprehensive knowledge of all your account's root users and their configurations is invaluable for maintaining a secure AWS environment. Instant access to this information allows cloud teams to promptly identify any unauthorized or suspicious activities associated with root accounts. This visibility enables timely responses to potential security breaches and aids in enforcing proper security measures.
To find all information about your root users, head to IAM tab on the console screen. Now you should be able to see multiple sub-tabs. Select the Root Users subtab and the first view is summary of all root users.
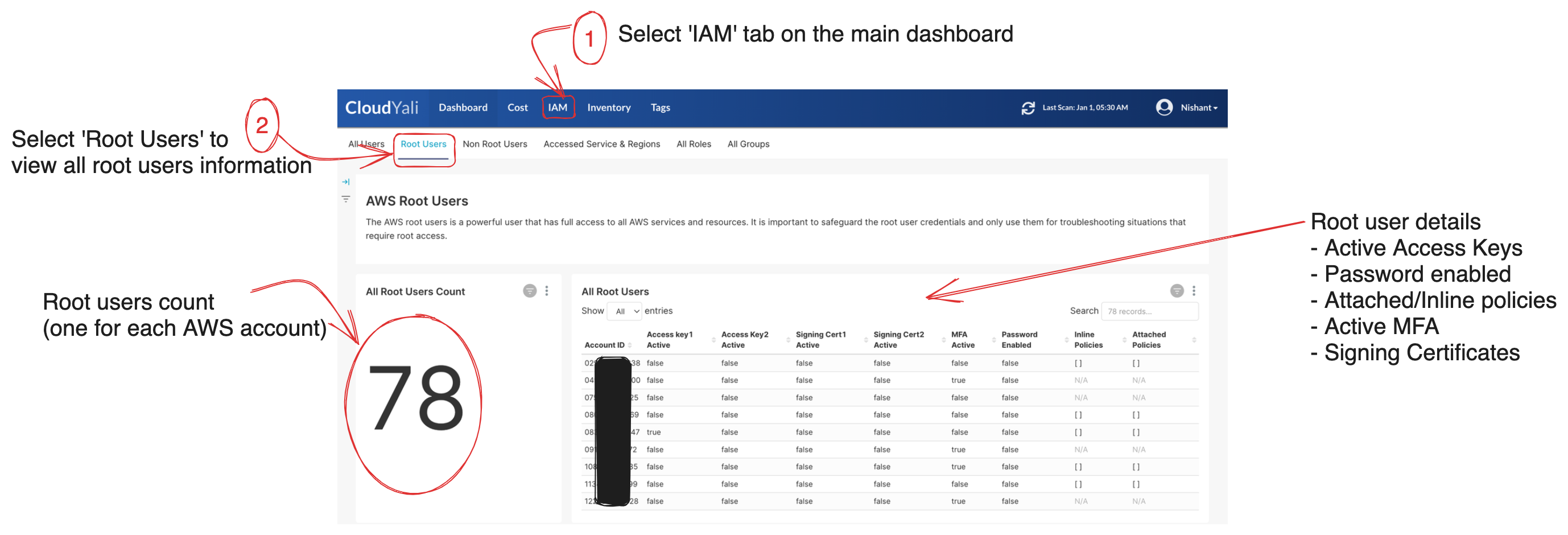
In this view you may get the details such as:
- If any active access keys are present for root user.
- Signing certificates information, such as if any signing certificate is in use or not
- If password is enabled or not
- Is MFA used for signin
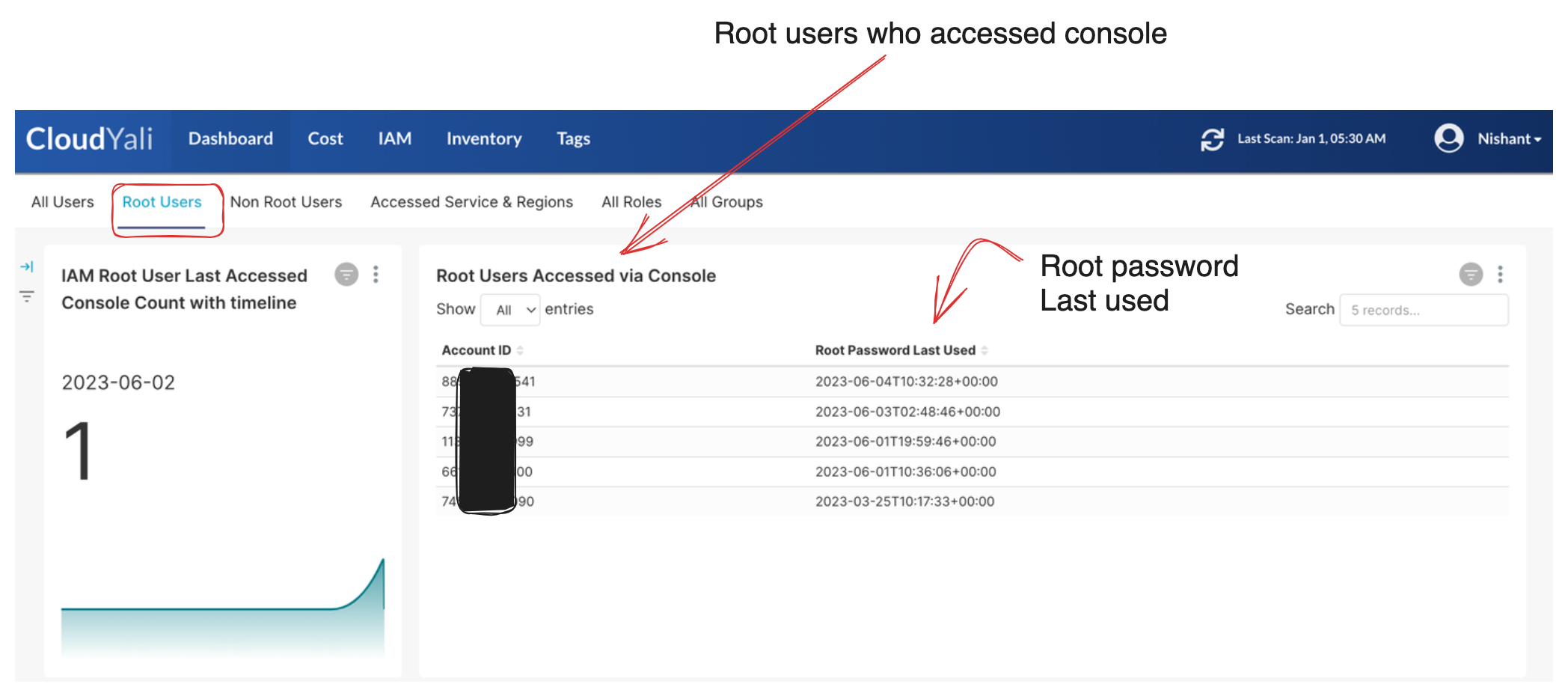
Root users accessed via console
This view helps cloud admins to understand if any root user is used to login into the AWS console and if yes, at what time.
One of the crucial controls for managing the AWS root user is monitoring its console access. It is essential to track whether the root user has been accessed recently and, if so, to determine whether the access was for a legitimate purpose. Given the root user's complete control over the AWS account, it is imperative to refrain from using it for daily activities.
The root user should be used to login in only exceptional cases. For daily admin activities create an admin user.
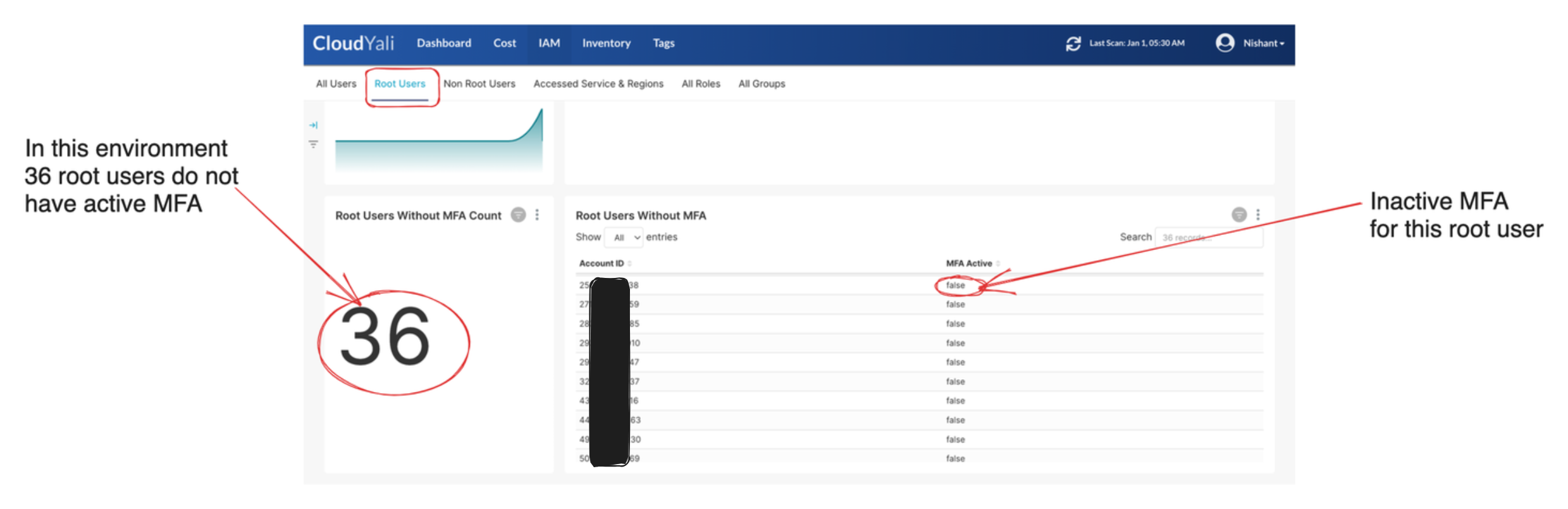
Root users without MFA
This view helps cloud admin identify root users without an active MFA.
Enabling multi-factor authentication (MFA) for root users is a crucial step in enhancing the security of your AWS environment. To further bolster the account's security, consider utilizing a physical hardware MFA device, such as a YubiKey, instead of relying solely on standard authenticator phone apps.
Safeguarding the root account credentials becomes paramount. You can write down the password on a piece of paper and print out backup MFA codes, storing them in a secure location such as a fireproof safe.
If you have a root user without active MFA, immediately ensure to have MFA activated. Not having an active MFA is a serious security problem.
It is important to note that accounts created through AWS Organizations also require MFA. For root users, the password recovery workflow is the only method available to set up MFA.
To simplify MFA management for multiple child accounts, organizations often employ a single mailbox, such as
aws@yourcompany.io, by using variations likeaws+dev@yourcompany.ioandaws+staging@yourcompany.io. This approach simplifies the management of MFA for the child accounts, allowing you to work with a single MFA device. However, it is crucial to apply stringent security measures to protect the mailbox, given its critical role in securing the AWS accounts. For further insights into root user management and MFA practices, we recommend reading Scott Piper's insightful article on the subject.
Root users with access keys
This view helps cloud admin identify root users with programmatic access keys. For each IAM user, at max two accesss keys can be activated. This view helps to identify which access keys are active.
Enabling programmatic access keys for the root users introduces unnecessary vulnerabilities, providing an additional entry point for potential hackers. Considering that the root user is rarely utilized for API access, there is no justification for granting it API permissions. It is highly recommended to refrain from adding a programmatic access key to the root user and, if one exists, promptly delete any associated API tokens.
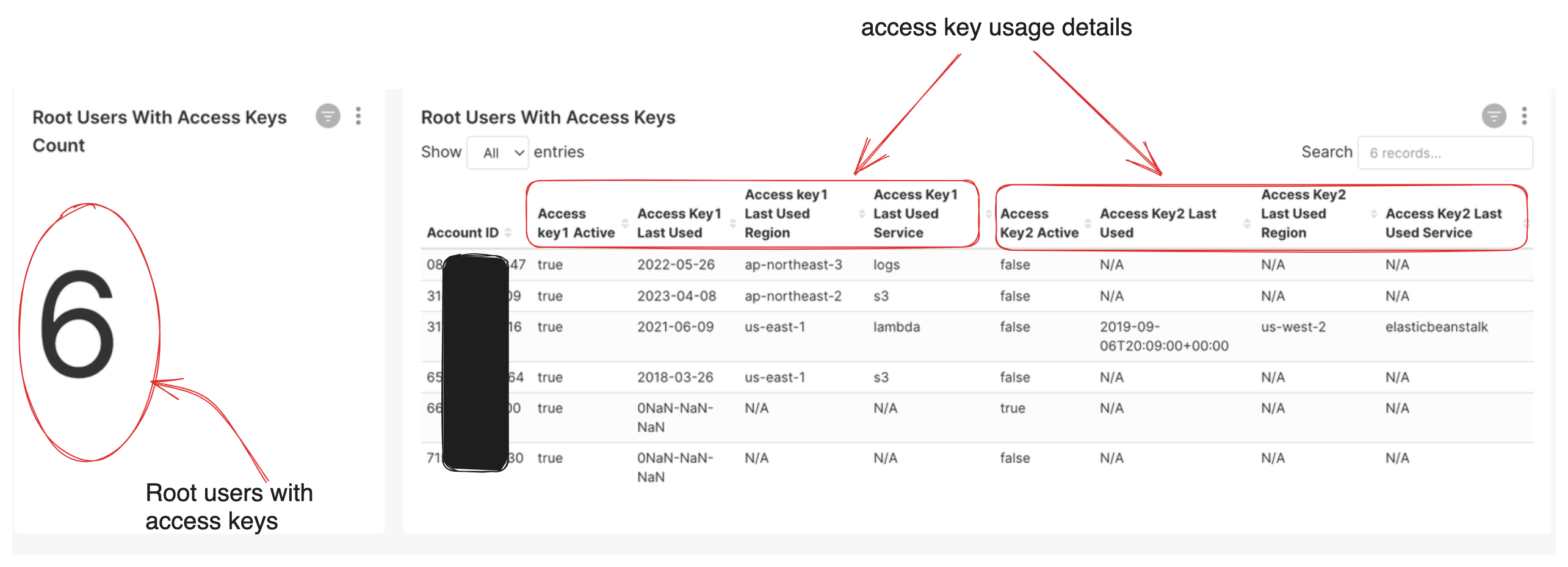
By proactively disabling access keys for the root user, organizations can significantly reduce the attack surface and enhance the overall security of their AWS environment. Eliminating unnecessary access keys minimizes the risk of unauthorized API access and fortifies the protection of critical resources and sensitive data.