Monitoring IAM Roles
The IAM roles help to assign permissons to the trusted IAM users or other IAM roles. IAM roles are also used to establish the trust relationship with other accounts. Obviously, this has third-party risk-management implications, and all third-party access should be reviewed.
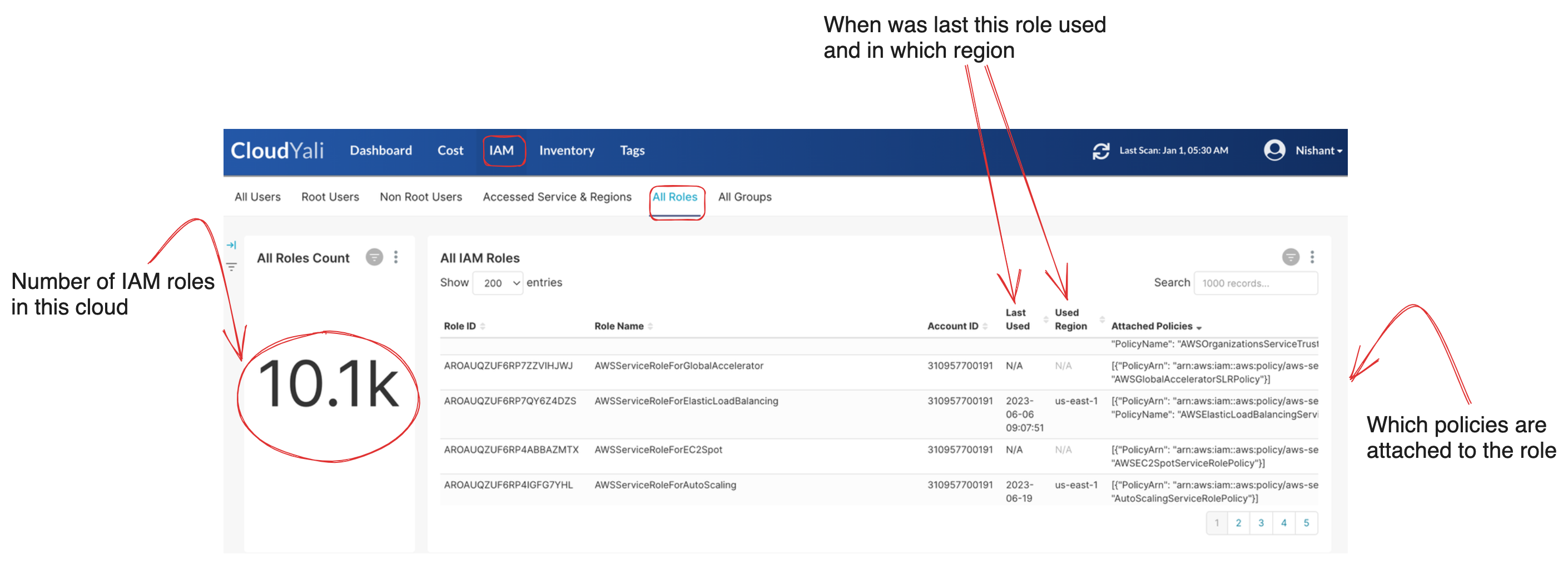
All IAM roles details
This view helps cloud team to get the details such as all available IAM roles in cloud, the last used region and time, and what policies are attached to the role.
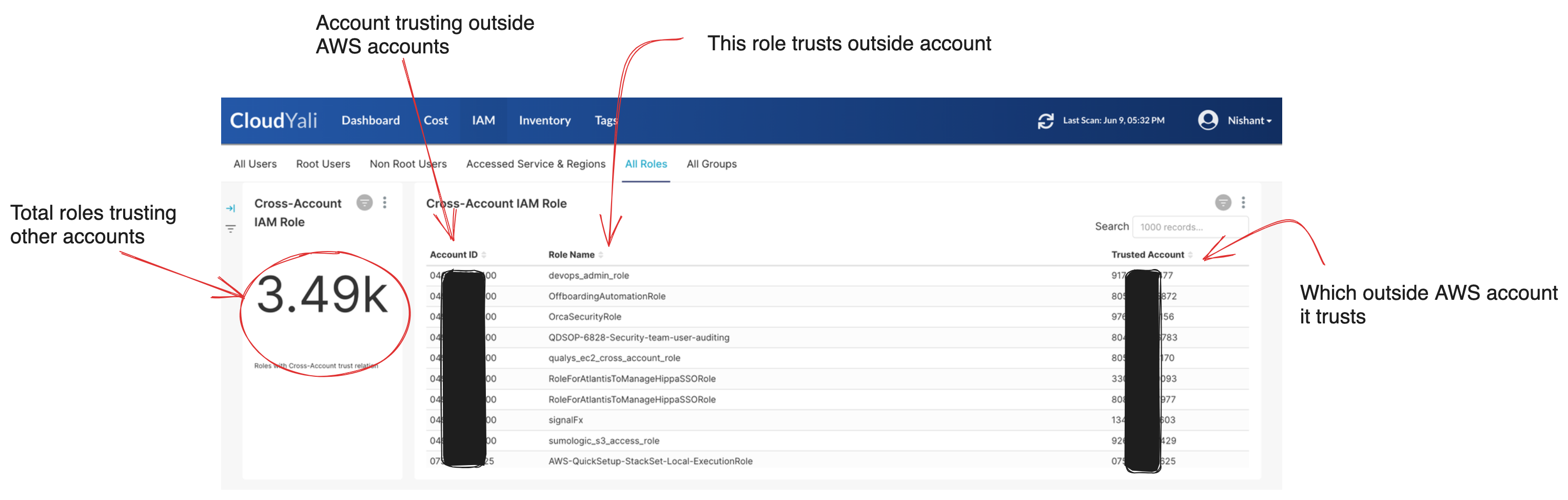
Cross account roles
This view helps cloud admin to identify all IAM roles which trust other AWS accounts.
With AWS IAM, you can grant other AWS customers access to perform actions in your account. Obviously, this has third-party risk-management implications, and all third-party access should be reviewed.
Within an AWS organization, there are often a lot of cross-account trusts. Various accounts are created to audit configuration, write logs, perform auto-remediation tasks, or deploy resources via a centralized pipeline. These are not third-party risks.
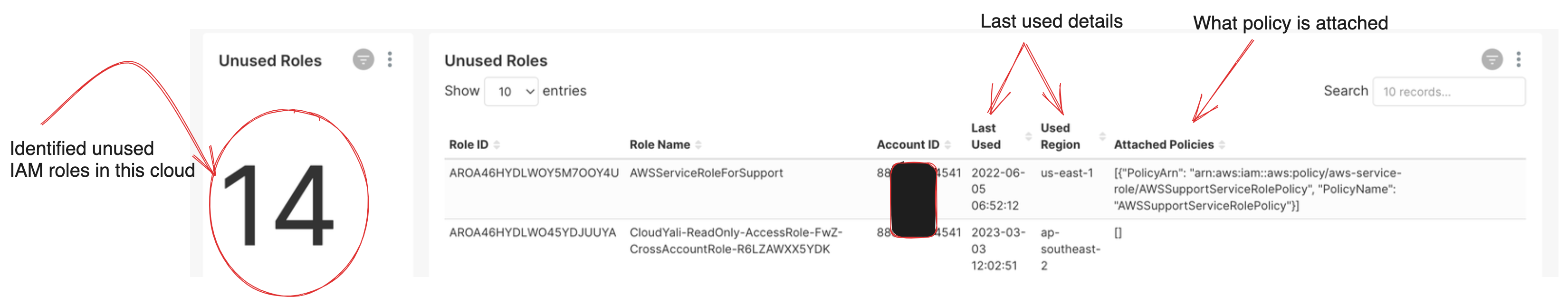
Unused IAM roles
This view helps cloud admin to identify all IAM roles which have not been used since last 90 days.
Periodically ensuring that all the resources you’ve created are still being used can reduce operational complexity by eliminating the need to track unnecessary resources. It also improves security: identifying unused IAM roles helps reduce the potential for improper or unintended access to your critical infrastructure and workloads.
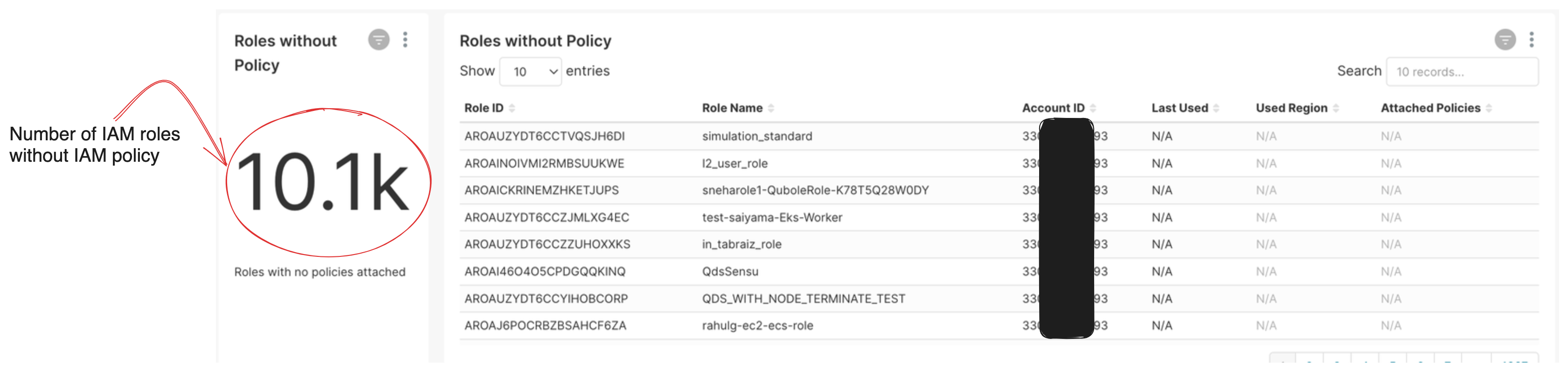
Roles without policies
This view helps cloud admin to identify all IAM roles without any attached policy.